Fuzzing Foxit Reader
signal-labs 블로그에서 Foxit Reader 대상으로 퍼징하는 글을 보게 됐다. 구글링 해보니 Foxit Reader를 타겟으로 퍼징하는 몇 개의 글을 더 찾을 수 있었다.
- Wrapping the Converter within Foxit Reader
- Try to write a wrapper for the ConvertToPDF function of foxit reader
- Fuzzing FoxitReader 9.7's ConvertToPDF
- FICFuzzingHarness: Foxit Image Converter Fuzzing Harness
1. WRAPPING THE CONVERTER WITHIN FOXIT READER
ZDI 블로그에 게시된 글로 Foxit Reader 7.3.4 버전에서 이미지 파일을 PDF로 변환하는 모듈을 퍼징하는 내용을 다룬다. 타겟 모듈은 ConvertToPDF_x86.dll 파일이고 위의 모든 링크가 이 DLL 파일을 타겟으로 퍼징하는 내용이다.
기억을 더듬어보면, 블로그에 글이 등록됐을때 퍼징에는 특별한 관심이 없었고 ConvertToPDF_x86.dll 라이브러리를 파이썬으로 편하게 사용할 수 있는 정도로 보고 넘어간 거 같다. 글 내용을 봐도 가상함수(virtual function) 호출할 때 사용하는 인자나 구조체의 정보를 얻는 등의 분석적인 성격의 내용은 없다. 동영상에서 ConvertToPDF_Fuzz.py 퍼저를 만들어 사용한 것을 볼 수 있는데 코드는 공개하지 않았다. @symeonp가 글을 보고 구현한 코드는 아래 링크에서 볼 수 있다. 제대로 작동하지 않는다.
2. 试写FOXIT READER的CONVERTTOPDF功能的WRAPPER
(English: TRY TO WRITE A WRAPPER FOR THE CONVERTTOPDF FUNCTION OF FOXIT READER)
ZDI 블로그에서 다룬 내용과 같은 Foxit Reader 7.3.4 버전을 타겟으로 퍼징한 내용이다. WinAFL을 사용해 퍼징을 수행했고 harness 코드도 공개했다. 가상함수 InitPdfConverter, InitPrinter, ConvertToPdf를 식별하고 인자 확인 및 호출순서 등의 내용을 기술하고 있다.

3. Fuzzing FoxitReader 9.7’s ConvertToPDF
2번 글을 보고 Foxit Reader 9.7 버전을 타겟으로 퍼징하는 내용이다. 7.3.4 버전과는 함수 호출 등 여러 부분에서 변화가 생겼고 그에 맞춰 harness 코드를 다듬었다는 내용을 간략하게 설명하는 글이다.
cout << "Applying converter_buf changes\n";
const wchar_t* foxitVer = L"Foxit Reader Printer Version 9.7.1.2227";
wcsncpy(converter_buf + (0xb68 / 2), foxitVer, wcslen(foxitVer));가상함수 ConvertToPdf 함수는 첫 번째 인자로 버퍼(buffer)를 받는데 이 버퍼에는 input_file, output_file 등의 정보가 담겨 있다. buffer 앞 4바이트 값(아래 그림에서 주소 03a45690)은 어떤 주소이고 FoxitReader.exe 프로세스 영역에 속한다. 글쓴이는 이 값이 무엇인지 정확하게 모르겠지만 어쨌든 FoxitReader.exe 프로세스를 로드하는 다소 무모한(?) 방법을 사용했다..
아래 FICFuzzingHarness에서 다루겠지만 이 4바이트(03a45690)는 메모리 할당/해제 함수포인터를 담고 있는 구조체다.

harness 소스코드를 보면 알 수 있듯이 FoxitReader.exe를 로드하더니 더 나아가 IAT(Import Address Table)에 있는 모든 DLL을 로드한다, 와우. anyway, 학습하는 자에게는 소중한 글임은 분명하다.
4. FICFuzzingHarness: Foxit Image Converter Fuzzing Harness
@NattiSamson가 공개한 Foxit Reader 9.7.1.29511 버전을 타겟으로 한 harness다. Foxit Reader 10부터는 이미지 변환 모듈이 Foxit Reader에서 제거됐고 Foxit PhantomPDF로 옮겨 갔다고 한다. 즉, ConvertToPDF_x86.dll 라이브러리가 더 이상 Foxit Reader에 포함되지 않는다.
Foxit Image Converter Fuzzing Harness
Since foxit ended up disabling and removing the parsing code of the Image Converter Module, starting from the latest Foxit Reader (Version 10.0.0.35798), I made my fuzzing harness publicly avilable.
**Note:** The Image Convertor module is still avilable on the Foxit PhantomPDF.
**The Harness is developed for:** Foxit Reader version 9.7.1.29511harness 소스코드도 재미있다. 하네스에서 thiscall을 구현하기 귀찮았는지, 모든 함수 호출을 __asm 키워드 안에서 어셈블리코드를 통해 수행하는 것을 볼 수 있다.
__asm
{
mov ecx,thispointer
mov edx,vtable
lea edi,printerName
push edi
call Function2
mov Result,eax
} signal-lab의 harness와 달리 buffer 앞 4바이트가 가리키는 주소에 메모리 할당/복사, 해제를 위한 함수 주소가 존재한다는 것을 알고 harness를 구현했다. 따라서 해당 목적에 맞게 함수만 구현하면 되기에 FoxitReader.exe 프로세스를 로드하는 일은 하지 않았다.
5. And More, My Fuzzer
이렇게 연관있는 몇 개의 글을 읽고 보고 나니 harness를 조금 더 다듬어서 사용 할 수 있겠다는 생각이 들었다.
Function calls
앞서 본 여러 harness 소스코드를 통해 ConverToPDF_x86.dll 라이브러리 로드 후의 함수 호출 순서를 확인했지만 windbg를 통해 다시 한번 전체 흐름을 살펴보기로 했다. windbg 디버거로 FoxitReader.exe 프로세스에 어태치 한 후 ConvertToPDF_x86.dll 라이브러리의 모든 함수에 브레이크포인트를 설정하고 관찰했다.
0:008> bm ConvertToPDF_x86!*
1: 5a7d1cc0 @!"ConvertToPDF_x86!CreateFXPDFConvertor"
2: 5a7d1d80 @!"ConvertToPDF_x86!CreateFXURLToHtml"
3: 5a7d1e10 @!"ConvertToPDF_x86!DestorFXPDFConvertor"
4: 5a7d1f70 @!"ConvertToPDF_x86!GetFileType_"
5: 5a7d2f00 @!"ConvertToPDF_x86!ReleaseFXURLToHtml"
6: 5ab97100 @!"ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_AddDrmPermission"
7: 5ab97190 @!"ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_SendEmailNotification"미리 준비한 그림 파일 Capture.PNG을 FoxitReader에 드래그하면, 이미지 파일을 PDF로 변환하면서 위 함수들이 호출된다. 이 중 CreateFXPDFConvertor 함수는 Convertor 객체를 리턴하는데 객체 가상함수 테이블(vftable)에 있는 모든 함수에 위와 같이 브레이크포인트를 설정한다.
0:000> dd eax // CreateFXPDFConvertor 함수가 리턴한 Convertor 객체
4183afc8 5ac02f30 00000000 c0c0c000 00000000
4183afd8 c0c0c000 00000001 00000000 00000000
4183afe8 00000000 c0c0c000 00000000 00000000
4183aff8 00000000 d0d0d0d0 ???????? ????????
4183b008 ???????? ???????? ???????? ????????
4183b018 ???????? ???????? ???????? ????????
4183b028 ???????? ???????? ???????? ????????
4183b038 ???????? ???????? ???????? ????????
0:000> dps 5ac02f30 la
5ac02f30 5a7d1590 ConvertToPDF_x86+0x31590
5ac02f34 5a7d2640 ConvertToPDF_x86!GetFileType_+0x6d0
5ac02f38 5a7d3170 ConvertToPDF_x86!ReleaseFXURLToHtml+0x270
5ac02f3c 5a7d2fd0 ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0
5ac02f40 5a7d2930 ConvertToPDF_x86!GetFileType_+0x9c0
5ac02f44 5a7d1eb0 ConvertToPDF_x86!DestorFXPDFConvertor+0xa0
5ac02f48 5a7d1e50 ConvertToPDF_x86!DestorFXPDFConvertor+0x40
5ac02f4c 5a7d2cd0 ConvertToPDF_x86!GetFileType_+0xd60
5ac02f50 5a7d2f30 ConvertToPDF_x86!ReleaseFXURLToHtml+0x30
5ac02f54 5a7d2d10 ConvertToPDF_x86!GetFileType_+0xda0
// set breakpoint on virtual functions
0:000> bp 5a7d1590
0:000> bp 5a7d2640
0:000> bp 5a7d3170
0:000> bp 5a7d2fd0
0:000> bp 5a7d2930
0:000> bp 5a7d1eb0
0:000> bp 5a7d1e50
0:000> bp 5a7d2cd0
0:000> bp 5a7d2f30
0:000> bp 5a7d2d10
0:000> g관찰 결과, 가상함수 테이블에 있는 모든 함수가 호출되지는 않았다. windbg, IDA를 적절히 짬뽕해서 분석했으며 아래와 같이 호출된 함수들은 적절한 이름을 붙였다.
5a7d1590 ConvertToPDF_x86+0x31590 <== vfunc1(ConvertToPDF)
5a7d2640 ConvertToPDF_x86!GetFileType_+0x6d0 <== vfunc2(FoxitSDKMsgStart)
5a7d3170 ConvertToPDF_x86!ReleaseFXURLToHtml+0x270 <== vfunc3(InitPrinter)
5a7d2fd0 ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0 <== vfunc4(InitPDFConvertor)
5a7d2930 ConvertToPDF_x86!GetFileType_+0x9c0 <== vfunc5(not called)
5a7d1eb0 ConvertToPDF_x86!DestorFXPDFConvertor+0xa0 <== vfunc6(not called)
5a7d1e50 ConvertToPDF_x86!DestorFXPDFConvertor+0x40 <== vfunc7(not called)
5a7d2cd0 ConvertToPDF_x86!GetFileType_+0xd60 <== vfunc8(not called)
5a7d2f30 ConvertToPDF_x86!ReleaseFXURLToHtm <== vfunc9(not called)
5a7d2d10 ConvertToPDF_x86!GetFileType_+0xda0 <== vfunc10(Release)PNG를 PDF로 변환하면서 호출하는 함수 순서, 객체 정보 등을 확인한 windbg 로그는 글 가장 밑에 첨부했다. Convertor 객체 가상함수 ConvertToPDF는 실질적인 변환을 담당하는 함수이며 첫 번째 인자로 받는 버퍼(buffer)에서 input, output 등의 정보를 가져온다.
// check input buffer
0:002> db 3c3621b0
3c3621b0 40 96 bf 03 0b 00 00 00-00 00 00 00 00 00 00 00 @...............
3c3621c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362200 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362210 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362220 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// printer name
0:002> db 3c3621b0+0xb68
3c362d18 46 00 6f 00 78 00 69 00-74 00 20 00 52 00 65 00 F.o.x.i.t. .R.e.
3c362d28 61 00 64 00 65 00 72 00-20 00 50 00 72 00 69 00 a.d.e.r. .P.r.i.
3c362d38 6e 00 74 00 65 00 72 00-20 00 56 00 65 00 72 00 n.t.e.r. .V.e.r.
3c362d48 73 00 69 00 6f 00 6e 00-20 00 39 00 2e 00 37 00 s.i.o.n. .9...7.
3c362d58 2e 00 30 00 2e 00 32 00-32 00 32 00 30 00 00 00 ..0...2.2.2.0...
3c362d68 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362d78 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362d88 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// input path (C:\Users\pdpd\Desktop\Capture.PNG)
0:002> db 3c3621b0+1624
3c3637d4 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
3c3637e4 5c 00 70 00 64 00 70 00-64 00 5c 00 44 00 65 00 \.p.d.p.d.\.D.e.
3c3637f4 73 00 6b 00 74 00 6f 00-70 00 5c 00 43 00 61 00 s.k.t.o.p.\.C.a.
3c363804 70 00 74 00 75 00 72 00-65 00 2e 00 50 00 4e 00 p.t.u.r.e...P.N.
3c363814 47 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 G...............
3c363824 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363834 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363844 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// output path (C:\Users\pdpd\AppData\Local\Temp\FOX8C6E.pdf)
0:002> db 3c3621b0+182c
3c3639dc 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
3c3639ec 5c 00 70 00 64 00 70 00-64 00 5c 00 41 00 70 00 \.p.d.p.d.\.A.p.
3c3639fc 70 00 44 00 61 00 74 00-61 00 5c 00 4c 00 6f 00 p.D.a.t.a.\.L.o.
3c363a0c 63 00 61 00 6c 00 5c 00-54 00 65 00 6d 00 70 00 c.a.l.\.T.e.m.p.
3c363a1c 5c 00 46 00 4f 00 58 00-38 00 43 00 36 00 45 00 \.F.O.X.8.C.6.E.
3c363a2c 2e 00 70 00 64 00 66 00-00 00 00 00 00 00 00 00 ..p.d.f.........
3c363a3c 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363a4c 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// some data, i don't know
0:002> db 3c3621b0+1e4c
3c363ffc 07 00 00 00 ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ....????????????
3c36400c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36401c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36402c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36403c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36404c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36405c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36406c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
0:002> g다행히 변환의 시작부터 끝까지 과정이 그리 길지 않았다. 함수 호출 순서는 아래와 같다.
- GetFileType_ 함수로 input file의 형식을 구한다. 파일명으로 타입을 판단하더라..
- CreateFXPDFConvertor
- InitPDFConvertor
- FoxitSDKMsgStart
- InitPrinter
- ConvertToPDF
- allocateCallback
- deallocateCallBack
- DestorFXPDFConvertor
위 순서로 함수가 호출되고 Foxit Reader에 변환된 PDF 파일이 로드된다.
Memory callback functions
Convertor->ConvertToPDF 함수 첫 번째 인자 buffer의 앞 4바이트, 즉 *(unsigned int *)&buffer는 포인터이며 이 포인터를 따라가면 메모리 할당, 해제 루틴을 가리키는 함수주소가 존재한다.
typedef struct memVftable_t {
void* deallocate;
void* allocate;
} MemVftable;Convertor->ConvertToPDF 함수는 위의 두 함수를 사용해서 버퍼를 생성, 복사, 해제 등 작업을 한다.
0:002> dps 3c3621b0 l4 // ConvertToPDF 함수의 첫 번째 인자
3c3621b0 03bf9640 FoxitReader!std::basic_streambuf<char,std::char_traits<char> >::`vftable'+0x7dbe4
3c3621b4 0000000b
3c3621b8 00000000
3c3621bc 00000000
0:002> dps 03bf9640
03bf9640 013eb1c0 FoxitReader!CryptUIWizExport+0x573640
03bf9644 013eb430 FoxitReader!CryptUIWizExport+0x5738b0Harness
마지막으로 IDA를 통해 각 함수의 인자 정보를 파악했고, windbg에서 확인한 함수호출 순서대로 harness를 작성했다.
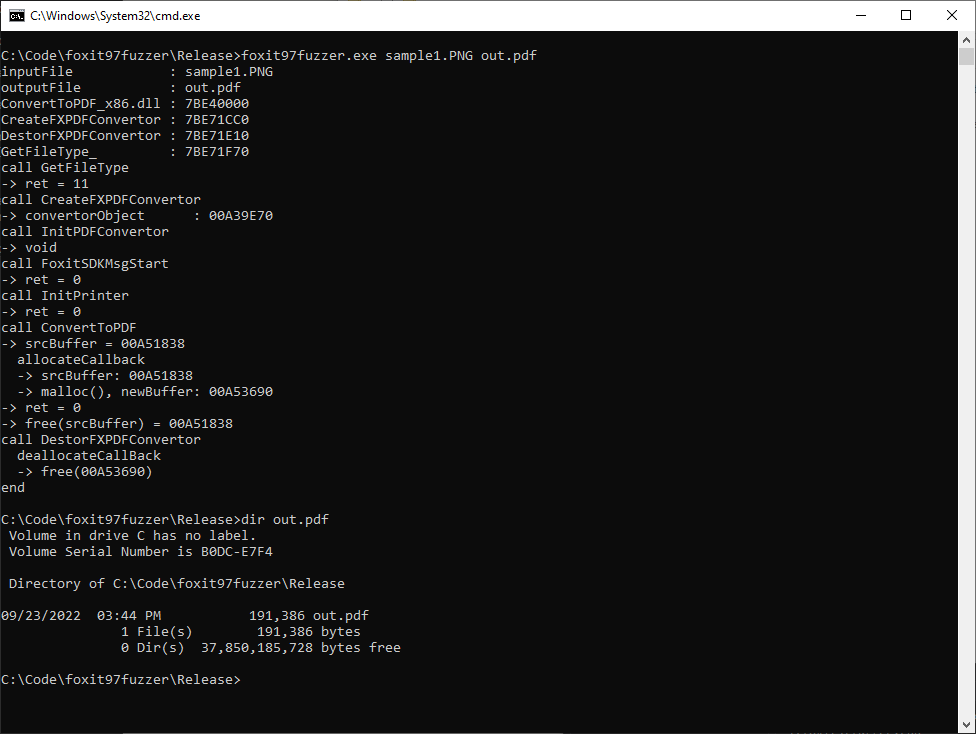
PNG 파일을 PDF로 변환하는 기능만 담은 harness를 작성했으니 이제 본격적인 퍼징을 해 볼 차례다. 앞선 연구들이 모두 WinAFL을 사용한 것과 달리 jackalope fuzzer를 사용했다.
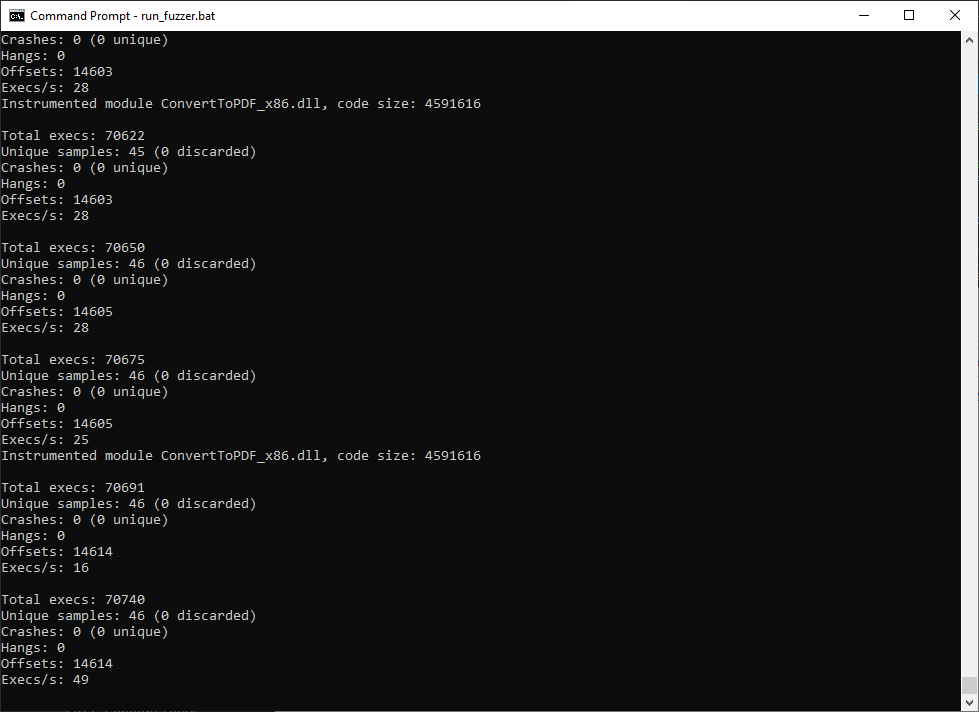
우선 input으로 PNG 파일 하나만 주고 퍼징을 시작했다.
Result
2-3시간 정도 돌렸을 때 결과는 이렇다.

windbg command log
0:007> g
(392c.bc4): Break instruction exception - code 80000003 (first chance)
eax=0600e000 ebx=00000000 ecx=7779df50 edx=7779df50 esi=7779df50 edi=7779df50
eip=77764d30 esp=4a96fdec ebp=4a96fe18 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
ntdll!DbgBreakPoint:
77764d30 cc int 3
0:008> bm ConvertToPDF_x86!*
1: 5a7d1cc0 @!"ConvertToPDF_x86!CreateFXPDFConvertor"
2: 5a7d1d80 @!"ConvertToPDF_x86!CreateFXURLToHtml"
3: 5a7d1e10 @!"ConvertToPDF_x86!DestorFXPDFConvertor"
4: 5a7d1f70 @!"ConvertToPDF_x86!GetFileType_"
5: 5a7d2f00 @!"ConvertToPDF_x86!ReleaseFXURLToHtml"
6: 5ab97100 @!"ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_AddDrmPermission"
7: 5ab97190 @!"ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_SendEmailNotification"
0:008> g
(392c.734): Unknown exception - code e0000001 (first chance)
(392c.734): Unknown exception - code e0000001 (first chance)
(392c.734): Unknown exception - code e0000001 (first chance)
// call GetTypeFile
Breakpoint 4 hit
eax=5a7d1f70 ebx=13ba8798 ecx=3afc4fbc edx=17ec6fbc esi=17ec6fbc edi=062fadc4
eip=5a7d1f70 esp=062fa33c ebp=062fa348 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
ConvertToPDF_x86!GetFileType_:
5a7d1f70 55 push ebp
0:000> gu
eax=0000000b ebx=13ba8798 ecx=2b9b2d72 edx=00000000 esi=17ec6fbc edi=062fadc4
eip=013e160b esp=062fa344 ebp=062fa348 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
FoxitReader!CryptUIWizExport+0x569a8b:
013e160b 8be5 mov esp,ebp
// GetFileType returns 0xb (input file is .PNG file)
0:000> r eax
eax=0000000b
0:000> g
// call CreateFXPDFConvertor
Breakpoint 1 hit
eax=5a7d1cc0 ebx=13ba8798 ecx=17ec6fbc edx=17ec6fbc esi=17ec6fbc edi=062fadc4
eip=5a7d1cc0 esp=062fa350 ebp=062fad88 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
ConvertToPDF_x86!CreateFXPDFConvertor:
5a7d1cc0 55 push ebp
0:000> gu
eax=4183afc8 ebx=13ba8798 ecx=00000000 edx=00000000 esi=17ec6fbc edi=062fadc4
eip=013dc083 esp=062fa354 ebp=062fad88 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
FoxitReader!CryptUIWizExport+0x564503:
013dc083 898540f9ffff mov dword ptr [ebp-6C0h],eax ss:002b:062fa6c8=39dd5f98
/*
CreateFXPDFConvertor returns convertor object(convertObject) with eax register.
First 4byte(0x5ac02f30) of object is address of vftable.
Set breakpoint ten(10) functions(ConvertToPDF_x86!*).
Ater analyzing with IDA disassembler, set function name like below.
5a7d1590 ConvertToPDF_x86+0x31590 <== vfunc1(ConvertToPDF)
5a7d2640 ConvertToPDF_x86!GetFileType_+0x6d0 <== vfunc2(FoxitSDKMsgStart)
5a7d3170 ConvertToPDF_x86!ReleaseFXURLToHtml+0x270 <== vfunc3(InitPrinter)
5a7d2fd0 ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0 <== vfunc4(InitPDFConvertor)
5a7d2930 ConvertToPDF_x86!GetFileType_+0x9c0 <== vfunc5(not called)
5a7d1eb0 ConvertToPDF_x86!DestorFXPDFConvertor+0xa0 <== vfunc6(not called)
5a7d1e50 ConvertToPDF_x86!DestorFXPDFConvertor+0x40 <== vfunc7(not called)
5a7d2cd0 ConvertToPDF_x86!GetFileType_+0xd60 <== vfunc8(not called)
5a7d2f30 ConvertToPDF_x86!ReleaseFXURLToHtm <== vfunc9(not called)
5a7d2d10 ConvertToPDF_x86!GetFileType_+0xda0 <== vfunc10(Release)
*/
0:000> dd eax
4183afc8 5ac02f30 00000000 c0c0c000 00000000
4183afd8 c0c0c000 00000001 00000000 00000000
4183afe8 00000000 c0c0c000 00000000 00000000
4183aff8 00000000 d0d0d0d0 ???????? ????????
4183b008 ???????? ???????? ???????? ????????
4183b018 ???????? ???????? ???????? ????????
4183b028 ???????? ???????? ???????? ????????
4183b038 ???????? ???????? ???????? ????????
0:000> dps 5ac02f30 la
5ac02f30 5a7d1590 ConvertToPDF_x86+0x31590
5ac02f34 5a7d2640 ConvertToPDF_x86!GetFileType_+0x6d0
5ac02f38 5a7d3170 ConvertToPDF_x86!ReleaseFXURLToHtml+0x270
5ac02f3c 5a7d2fd0 ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0
5ac02f40 5a7d2930 ConvertToPDF_x86!GetFileType_+0x9c0
5ac02f44 5a7d1eb0 ConvertToPDF_x86!DestorFXPDFConvertor+0xa0
5ac02f48 5a7d1e50 ConvertToPDF_x86!DestorFXPDFConvertor+0x40
5ac02f4c 5a7d2cd0 ConvertToPDF_x86!GetFileType_+0xd60
5ac02f50 5a7d2f30 ConvertToPDF_x86!ReleaseFXURLToHtml+0x30
5ac02f54 5a7d2d10 ConvertToPDF_x86!GetFileType_+0xda0
// set breakpoint on virtual functions
0:000> bp 5a7d1590
0:000> bp 5a7d2640
0:000> bp 5a7d3170
0:000> bp 5a7d2fd0
0:000> bp 5a7d2930
0:000> bp 5a7d1eb0
0:000> bp 5a7d1e50
0:000> bp 5a7d2cd0
0:000> bp 5a7d2f30
0:000> bp 5a7d2d10
0:000> g
// call 5a7d2fd0 (vfunc4, InitPDFConvertor)
Breakpoint 10 hit
eax=5a7d2fd0 ebx=13ba8798 ecx=4183afc8 edx=5ac02f30 esi=17ec6fbc edi=062fadc4
eip=5a7d2fd0 esp=062fa348 ebp=062fad88 iopl=0 nv up ei pl nz ac po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200212
ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0:
5a7d2fd0 55 push ebp
0:000> g
// call 5a7d2640 (vfunc2, FoxitSDKMsgStart)
Breakpoint 8 hit
eax=5a7d2640 ebx=13ba8798 ecx=4183afc8 edx=5ac02f30 esi=17ec6fbc edi=062fadc4
eip=5a7d2640 esp=062fa34c ebp=062fad88 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
ConvertToPDF_x86!GetFileType_+0x6d0:
5a7d2640 55 push ebp
// if succeed, FoxitSDKMsgStart returns 0(eax register) else it returns -10.
0:000> gu
eax=00000000 ebx=13ba8798 ecx=2db48e3a edx=0ac80000 esi=17ec6fbc edi=062fadc4
eip=013dc919 esp=062fa354 ebp=062fad88 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
FoxitReader!CryptUIWizExport+0x564d99:
013dc919 c645fc44 mov byte ptr [ebp-4],44h ss:002b:062fad84=39
0:000> g
// call 5a7d2640 (vfunc3, InitPrinter)
Breakpoint 9 hit
eax=5a7d3170 ebx=13ba8798 ecx=4183afc8 edx=5ac02f30 esi=17ec6fbc edi=062fadc4
eip=5a7d3170 esp=062fa34c ebp=062fad88 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
ConvertToPDF_x86!ReleaseFXURLToHtml+0x270:
5a7d3170 55 push ebp
// if succeed, InitPrinter returns 0(eax register) else it returns -9.
0:000> gu
eax=00000000 ebx=13ba8798 ecx=00000000 edx=13997ffc esi=17ec6fbc edi=062fadc4
eip=013dce0d esp=062fa354 ebp=062fad88 iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200246
FoxitReader!CryptUIWizExport+0x56528d:
013dce0d 898558f9ffff mov dword ptr [ebp-6A8h],eax ss:002b:062fa6e0=00000000
/*
call 5a7d1590 (vfunc1, ConvertToPDF)
Actual converting works in this function. Takes 13 arguments containing this(ECX) pointer.
The first(1st, 0x3c3621b0) argument is input buffer, contains datas/input_file/output_file and etc.
*/
0:000> g
Breakpoint 0 hit
eax=5a7d1590 ebx=425fafe8 ecx=4183afc8 edx=5ac02f30 esi=013dadb0 edi=425fafe8
eip=5a7d1590 esp=4a72f8d0 ebp=4a72f930 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000206
ConvertToPDF_x86+0x31590:
5a7d1590 55 push ebp
0:002> dps esp
4a72f8d0 013dae5a FoxitReader!CryptUIWizExport+0x5632da
4a72f8d4 3c3621b0
4a72f8d8 00000002
4a72f8dc f6c62bf6
4a72f8e0 4a72f8f4
...
// check input buffer
0:002> dps 3c3621b0 l4
3c3621b0 03bf9640 FoxitReader!std::basic_streambuf<char,std::char_traits<char> >::`vftable'+0x7dbe4
3c3621b4 0000000b
3c3621b8 00000000
3c3621bc 00000000
/*
check 4byte of input buffer, it's structure containg function pointer for memory(dealloc and alloc).
and this structure(0x03bf9640) is in FoxitReader.exe process.
0:002> lmvm FoxitReader*
Browse full module list
start end module name
00500000 05ec2000 FoxitReader (export symbols) C:\Program Files (x86)\Foxit Software\Foxit Reader\FoxitReader.exe
...
*/
0:002> dps 03bf9640
03bf9640 013eb1c0 FoxitReader!CryptUIWizExport+0x573640
03bf9644 013eb430 FoxitReader!CryptUIWizExport+0x5738b0
...
// set addtional breakpoint
0:002> bp 013eb1c0
0:002> bp 013eb430
0:002> bl
0 e Disable Clear 5a7d1590 0001 (0001) 0:**** ConvertToPDF_x86+0x31590
1 e Disable Clear 5a7d1cc0 0001 (0001) 0:**** ConvertToPDF_x86!CreateFXPDFConvertor
2 e Disable Clear 5a7d1d80 0001 (0001) 0:**** ConvertToPDF_x86!CreateFXURLToHtml
3 e Disable Clear 5a7d1e10 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor
4 e Disable Clear 5a7d1f70 0001 (0001) 0:**** ConvertToPDF_x86!GetFileType_
5 e Disable Clear 5a7d2f00 0001 (0001) 0:**** ConvertToPDF_x86!ReleaseFXURLToHtml
6 e Disable Clear 5ab97100 0001 (0001) 0:**** ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_AddDrmPermission
7 e Disable Clear 5ab97190 0001 (0001) 0:**** ConvertToPDF_x86!ConnectedPDF::ConnectedPDFSDK::FCP_SendEmailNotification
8 e Disable Clear 5a7d2640 0001 (0001) 0:**** ConvertToPDF_x86!GetFileType_+0x6d0
9 e Disable Clear 5a7d3170 0001 (0001) 0:**** ConvertToPDF_x86!ReleaseFXURLToHtml+0x270
10 e Disable Clear 5a7d2fd0 0001 (0001) 0:**** ConvertToPDF_x86!ReleaseFXURLToHtml+0xd0
11 e Disable Clear 5a7d2930 0001 (0001) 0:**** ConvertToPDF_x86!GetFileType_+0x9c0
12 e Disable Clear 5a7d1eb0 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor+0xa0
13 e Disable Clear 5a7d1e50 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor+0x40
14 e Disable Clear 5a7d2cd0 0001 (0001) 0:**** ConvertToPDF_x86!GetFileType_+0xd60
15 e Disable Clear 5a7d2f30 0001 (0001) 0:**** ConvertToPDF_x86!ReleaseFXURLToHtml+0x30
16 e Disable Clear 5a7d2d10 0001 (0001) 0:**** ConvertToPDF_x86!GetFileType_+0xda0
17 e Disable Clear 013eb1c0 0001 (0001) 0:**** FoxitReader!CryptUIWizExport+0x573640
18 e Disable Clear 013eb430 0001 (0001) 0:**** FoxitReader!CryptUIWizExport+0x5738b0
// check input buffer
0:002> db 3c3621b0
3c3621b0 40 96 bf 03 0b 00 00 00-00 00 00 00 00 00 00 00 @...............
3c3621c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362200 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362210 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362220 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// printer name
0:002> db 3c3621b0+0xb68
3c362d18 46 00 6f 00 78 00 69 00-74 00 20 00 52 00 65 00 F.o.x.i.t. .R.e.
3c362d28 61 00 64 00 65 00 72 00-20 00 50 00 72 00 69 00 a.d.e.r. .P.r.i.
3c362d38 6e 00 74 00 65 00 72 00-20 00 56 00 65 00 72 00 n.t.e.r. .V.e.r.
3c362d48 73 00 69 00 6f 00 6e 00-20 00 39 00 2e 00 37 00 s.i.o.n. .9...7.
3c362d58 2e 00 30 00 2e 00 32 00-32 00 32 00 30 00 00 00 ..0...2.2.2.0...
3c362d68 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362d78 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362d88 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// input path (C:\Users\pdpd\Desktop\Capture.PNG)
0:002> db 3c3621b0+1624
3c3637d4 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
3c3637e4 5c 00 70 00 64 00 70 00-64 00 5c 00 44 00 65 00 \.p.d.p.d.\.D.e.
3c3637f4 73 00 6b 00 74 00 6f 00-70 00 5c 00 43 00 61 00 s.k.t.o.p.\.C.a.
3c363804 70 00 74 00 75 00 72 00-65 00 2e 00 50 00 4e 00 p.t.u.r.e...P.N.
3c363814 47 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 G...............
3c363824 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363834 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363844 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// output path (C:\Users\pdpd\AppData\Local\Temp\FOX8C6E.pdf)
0:002> db 3c3621b0+182c
3c3639dc 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
3c3639ec 5c 00 70 00 64 00 70 00-64 00 5c 00 41 00 70 00 \.p.d.p.d.\.A.p.
3c3639fc 70 00 44 00 61 00 74 00-61 00 5c 00 4c 00 6f 00 p.D.a.t.a.\.L.o.
3c363a0c 63 00 61 00 6c 00 5c 00-54 00 65 00 6d 00 70 00 c.a.l.\.T.e.m.p.
3c363a1c 5c 00 46 00 4f 00 58 00-38 00 43 00 36 00 45 00 \.F.O.X.8.C.6.E.
3c363a2c 2e 00 70 00 64 00 66 00-00 00 00 00 00 00 00 00 ..p.d.f.........
3c363a3c 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c363a4c 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
// some data, i don't know
0:002> db 3c3621b0+1e4c
3c363ffc 07 00 00 00 ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ....????????????
3c36400c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36401c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36402c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36403c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36404c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36405c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c36406c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
0:002> g
/*
call 013eb430 (allocation function)
In this function, new buffer(0x1E50 size of object) is created.
Now, we have two buffer object.
object A - 0x3c3621b0
object B - 0x2e02b1b0 (created in this function)
And, copy fields of A into B object.
*/
Breakpoint 18 hit
eax=03bf9640 ebx=00000000 ecx=3c3621b0 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb430 esp=4a72f804 ebp=4a72f8cc iopl=0 nv up ei pl zr na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246
FoxitReader!CryptUIWizExport+0x5738b0:
013eb430 55 push ebp
0:002> p
...
eax=4a72f7f4 ebx=00000000 ecx=3c3621b0 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb458 esp=4a72f7e0 ebp=4a72f800 iopl=0 nv up ei ng nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000282
FoxitReader!CryptUIWizExport+0x5738d8:
013eb458 68501e0000 push 1E50h
0:002> p
eax=4a72f7f4 ebx=00000000 ecx=3c3621b0 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb45d esp=4a72f7dc ebp=4a72f800 iopl=0 nv up ei ng nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000282
FoxitReader!CryptUIWizExport+0x5738dd:
013eb45d e84bfaf401 call FoxitReader!CFXJSE_Arguments::GetValue+0xce6e1d (0333aead)
0:002> p
eax=2e02b1b0 ebx=00000000 ecx=00001e50 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb462 esp=4a72f7dc ebp=4a72f800 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202
FoxitReader!CryptUIWizExport+0x5738e2:
013eb462 83c404 add esp,4
0:002> db 2e02b1b0
2e02b1b0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1c0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1d0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1e0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1f0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b200 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b210 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b220 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> p
...
eax=3c3621b0 ebx=00000000 ecx=00001e50 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb478 esp=4a72f7e0 ebp=4a72f800 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202
FoxitReader!CryptUIWizExport+0x5738f8:
013eb478 50 push eax
0:002> db 2e02b1b0
2e02b1b0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1c0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1d0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1e0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1f0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b200 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b210 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b220 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> p
eax=3c3621b0 ebx=00000000 ecx=00001e50 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb479 esp=4a72f7dc ebp=4a72f800 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202
FoxitReader!CryptUIWizExport+0x5738f9:
013eb479 8b4df0 mov ecx,dword ptr [ebp-10h] ss:002b:4a72f7f0=2e02b1b0
0:002> db eax
3c3621b0 40 96 bf 03 0b 00 00 00-00 00 00 00 00 00 00 00 @...............
3c3621c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c3621f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362200 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362210 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
3c362220 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................
0:002> p
// copy fields of A into B object.
eax=3c3621b0 ebx=00000000 ecx=2e02b1b0 edx=00000000 esi=4183afc8 edi=3c3637d4
eip=013eb47c esp=4a72f7dc ebp=4a72f800 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202
FoxitReader!CryptUIWizExport+0x5738fc:
013eb47c e82fdcffff call FoxitReader!CryptUIWizExport+0x571530 (013e90b0)
0:002> p
// check fileds of B object.
eax=2e02b1b0 ebx=00000000 ecx=84e68f31 edx=3c363dee esi=4183afc8 edi=3c3637d4
eip=013eb481 esp=4a72f7e0 ebp=4a72f800 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000216
FoxitReader!CryptUIWizExport+0x573901:
013eb481 8945ec mov dword ptr [ebp-14h],eax ss:002b:4a72f7ec=3c3637d4
0:002> db 2e02b1b0
2e02b1b0 40 96 bf 03 0b 00 00 00-00 00 c0 c0 c0 c0 c0 c0 @...............
2e02b1c0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1d0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1e0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b1f0 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b200 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b210 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02b220 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> db 2e02b1b0+b68
2e02bd18 46 00 6f 00 78 00 69 00-74 00 20 00 52 00 65 00 F.o.x.i.t. .R.e.
2e02bd28 61 00 64 00 65 00 72 00-20 00 50 00 72 00 69 00 a.d.e.r. .P.r.i.
2e02bd38 6e 00 74 00 65 00 72 00-20 00 56 00 65 00 72 00 n.t.e.r. .V.e.r.
2e02bd48 73 00 69 00 6f 00 6e 00-20 00 39 00 2e 00 37 00 s.i.o.n. .9...7.
2e02bd58 2e 00 30 00 2e 00 32 00-32 00 32 00 30 00 00 00 ..0...2.2.2.0...
2e02bd68 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02bd78 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02bd88 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> db 2e02b1b0+1624
2e02c7d4 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
2e02c7e4 5c 00 70 00 64 00 70 00-64 00 5c 00 44 00 65 00 \.p.d.p.d.\.D.e.
2e02c7f4 73 00 6b 00 74 00 6f 00-70 00 5c 00 43 00 61 00 s.k.t.o.p.\.C.a.
2e02c804 70 00 74 00 75 00 72 00-65 00 2e 00 50 00 4e 00 p.t.u.r.e...P.N.
2e02c814 47 00 00 00 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 G...............
2e02c824 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02c834 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02c844 c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> db 2e02b1b0+182c
2e02c9dc 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.
2e02c9ec 5c 00 70 00 64 00 70 00-64 00 5c 00 41 00 70 00 \.p.d.p.d.\.A.p.
2e02c9fc 70 00 44 00 61 00 74 00-61 00 5c 00 4c 00 6f 00 p.D.a.t.a.\.L.o.
2e02ca0c 63 00 61 00 6c 00 5c 00-54 00 65 00 6d 00 70 00 c.a.l.\.T.e.m.p.
2e02ca1c 5c 00 46 00 4f 00 58 00-38 00 43 00 36 00 45 00 \.F.O.X.8.C.6.E.
2e02ca2c 2e 00 70 00 64 00 66 00-00 00 c0 c0 c0 c0 c0 c0 ..p.d.f.........
2e02ca3c c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
2e02ca4c c0 c0 c0 c0 c0 c0 c0 c0-c0 c0 c0 c0 c0 c0 c0 c0 ................
0:002> db 2e02b1b0+1e4c
2e02cffc 07 00 00 00 ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ....????????????
2e02d00c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d01c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d02c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d03c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d04c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d05c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02d06c ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
// run until exiting allocation function
// and go to next breakpoint
0:002> gu
eax=2e02b1b0 ebx=00000000 ecx=84e680e5 edx=3c363dee esi=4183afc8 edi=3c3637d4
eip=5a7d1774 esp=4a72f808 ebp=4a72f8cc iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000216
ConvertToPDF_x86+0x31774:
5a7d1774 8bc8 mov ecx,eax
0:002> g
// At this time, converting job is done, so it need to free two(A and B) objects
// call DestorFXPDFConvertor
Breakpoint 3 hit
eax=5a7d1e10 ebx=13ba8798 ecx=4183afc8 edx=17ec6fbc esi=17ec6fbc edi=062fadc4
eip=5a7d1e10 esp=062fa34c ebp=062fad88 iopl=0 nv up ei pl nz ac pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200216
ConvertToPDF_x86!DestorFXPDFConvertor:
5a7d1e10 56 push esi
0:000> gu
// Function DestorFXPDFConvertor calls deallocation functions
// In this function, two(A and B) objects is freed.
Breakpoint 16 hit
eax=5ac02f30 ebx=13ba8798 ecx=4183afc8 edx=17ec6fbc esi=00000000 edi=4183afc8
eip=5a7d2d10 esp=062fa340 ebp=062fad88 iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
ConvertToPDF_x86!GetFileType_+0xda0:
5a7d2d10 55 push ebp
0:000> g
// call 013eb1c0 (deallocation function)
Breakpoint 17 hit
eax=03bf9640 ebx=13ba8798 ecx=2e02b1b0 edx=0ac80000 esi=00000000 edi=4183afc8
eip=013eb1c0 esp=062fa328 ebp=062fa33c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
FoxitReader!CryptUIWizExport+0x573640:
013eb1c0 55 push ebp
0:000> g
// When deallocation function exit, we can see that object B is freed.
Breakpoint 17 hit
eax=013eb1c0 ebx=13ba8798 ecx=3c3621b0 edx=03bf9640 esi=17ec6fbc edi=062fadc4
eip=013eb1c0 esp=062fa32c ebp=062fa34c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200202
FoxitReader!CryptUIWizExport+0x573640:
013eb1c0 55 push ebp
0:000> db 2e02b1b0
2e02b1b0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b1c0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b1d0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b1e0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b1f0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b200 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b210 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
2e02b220 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
// go until deallocation function exit again, we can see that object A is freed.
0:000> gu
eax=3c3621b0 ebx=13ba8798 ecx=c8bbdbcd edx=0ac80000 esi=17ec6fbc edi=062fadc4
eip=013d3a7f esp=062fa334 ebp=062fa34c iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00200206
FoxitReader!CryptUIWizExport+0x55beff:
013d3a7f 8945e8 mov dword ptr [ebp-18h],eax ss:002b:062fa334=01f2cfa4
0:000> db 3c3621b0
3c3621b0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c3621c0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c3621d0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c3621e0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c3621f0 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c362200 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c362210 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
3c362220 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
0:000> g